Servers with Haskell and NixOS
Chris Martin
Monadic Party  2018 June 14-15
2018 June 14-15
The main idea
The Purely Functional Software Deployment Model, Eelco Dolstra, 2006
The main idea of the Nix approach is to store software components in isolation from each other in a central component store, under path names that contain cryptographic hashes of all inputs involved in building the component, such as /nix/store/rwmfbhb2znwp...-firefox1.0.4 […] this prevents undeclared dependencies and enables support for side-by-side existence of component versions and variants.
The hash is computed over all inputs, including the following:
- The sources of the components.
- The script that performed the build.
- Any arguments or environment variables passed to the build script.
- All build time dependencies, typically including the compiler, linker, any libraries used at build time, standard Unix tools such as
cp and tar, the shell, and so on.
Makefile
all: hilbert-curve.png
sourceUrl = https://archives.haskell.org/projects.haskell.org/diagrams/gallery/Hilbert.lhs
hilbert-curve.lhs:
wget $(sourceUrl) --output-document $@
hilbert-curve.svg: hilbert-curve.lhs
runhaskell --ghc-arg=-XTypeFamilies $< --output $@ --width 250
hilbert-curve.png: hilbert-curve.svg
convert $< $@
clean:
rm -f *.lhs *.svg *.png
.PHONY: clean
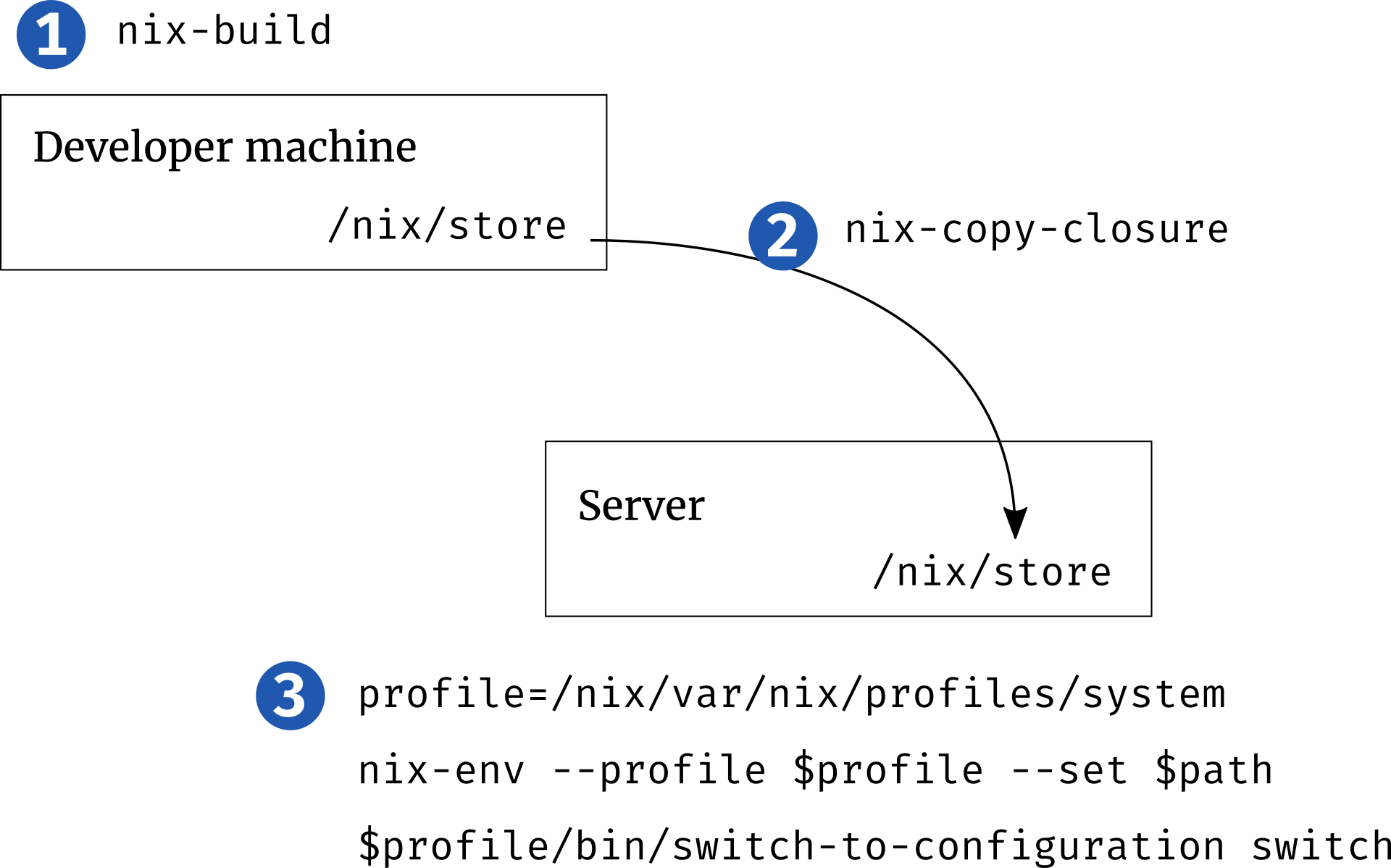
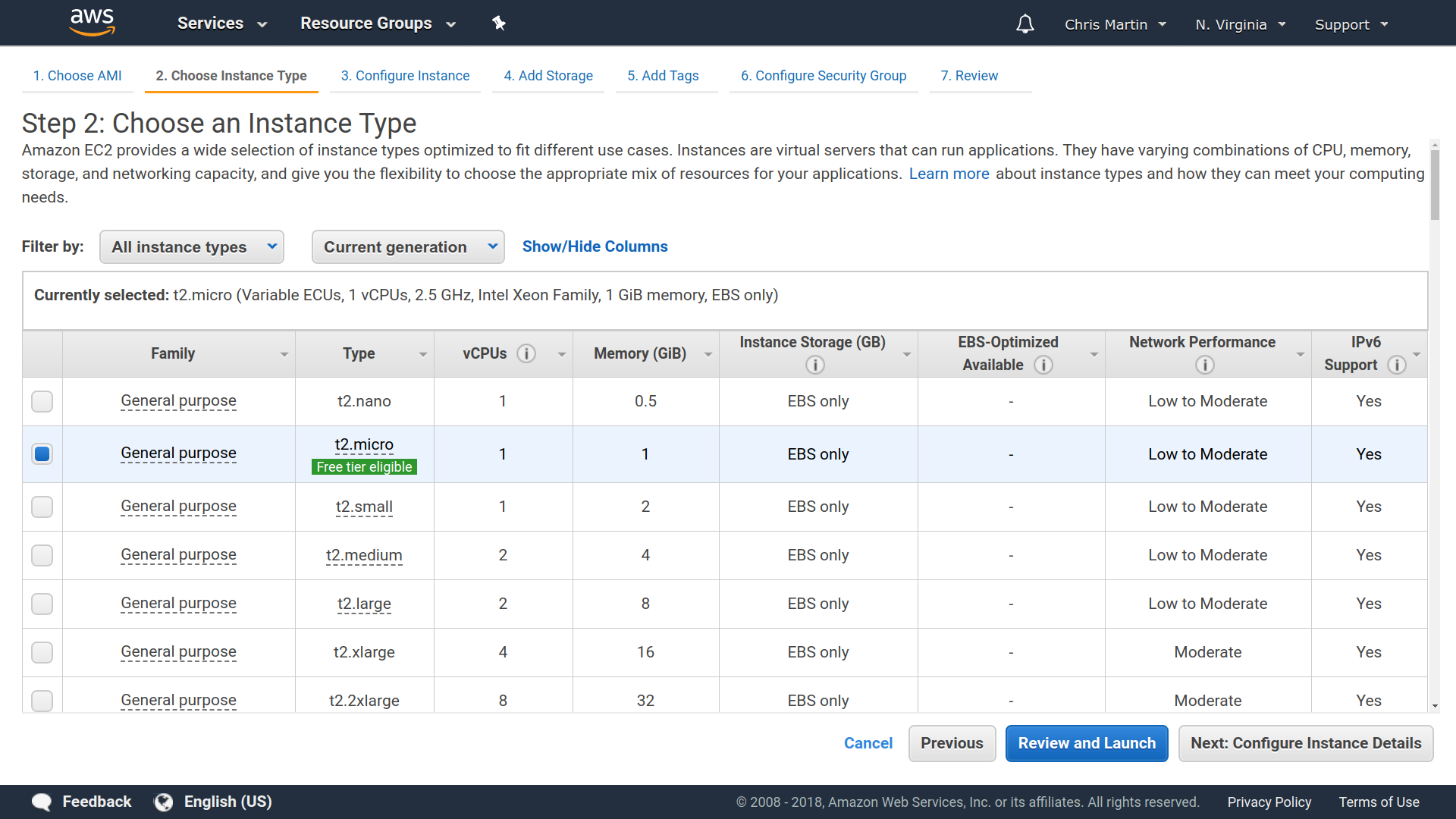
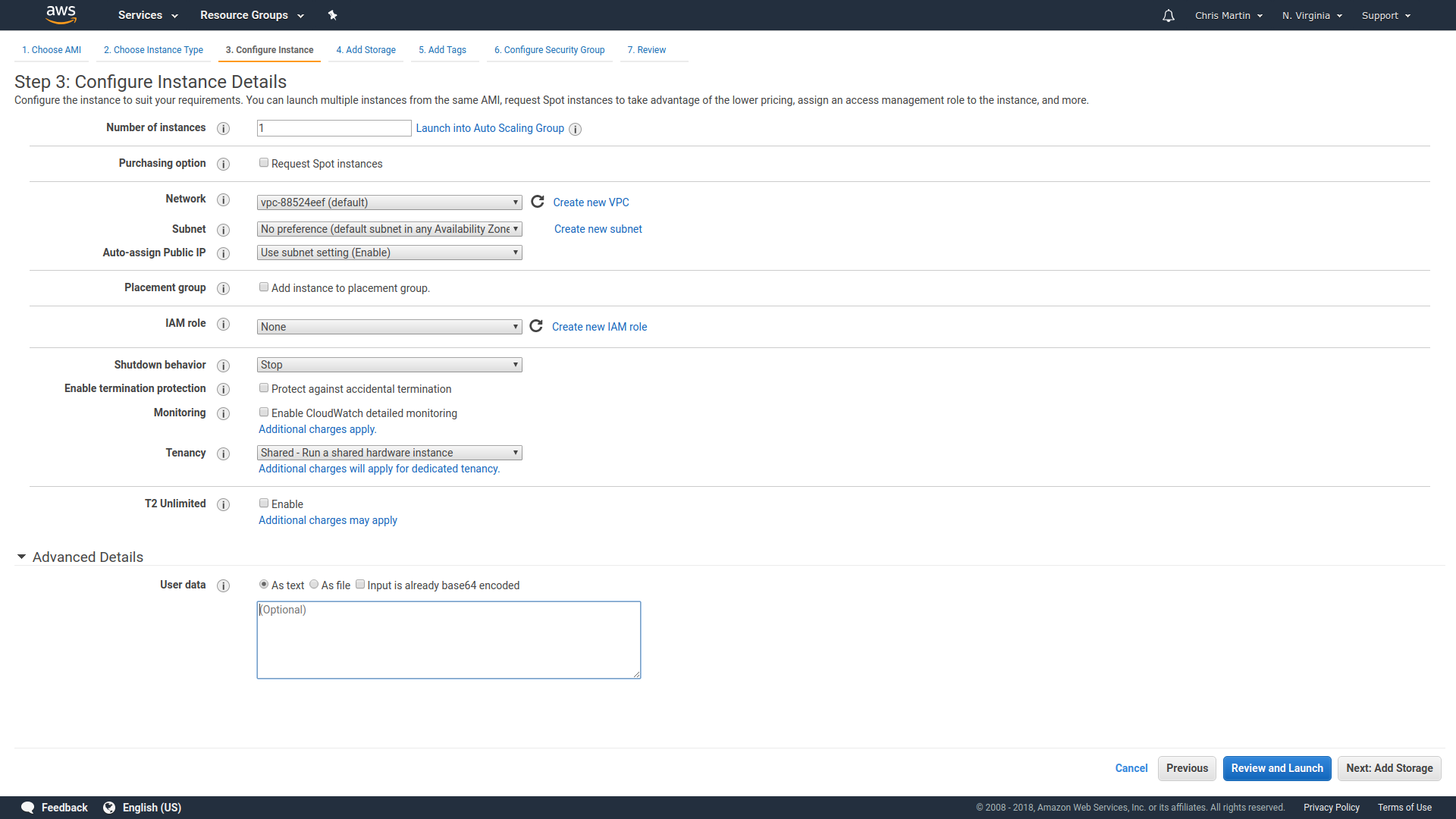
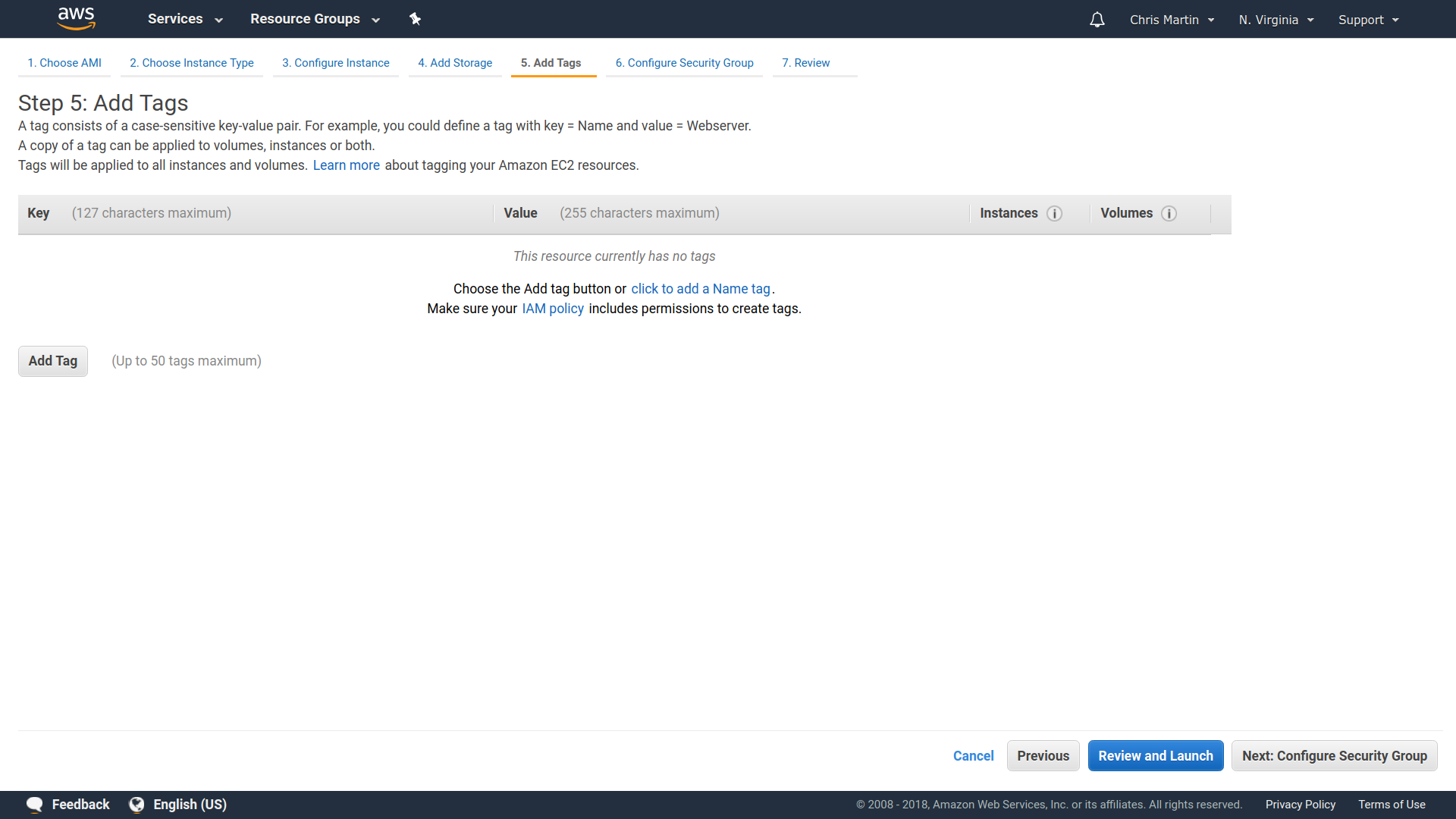
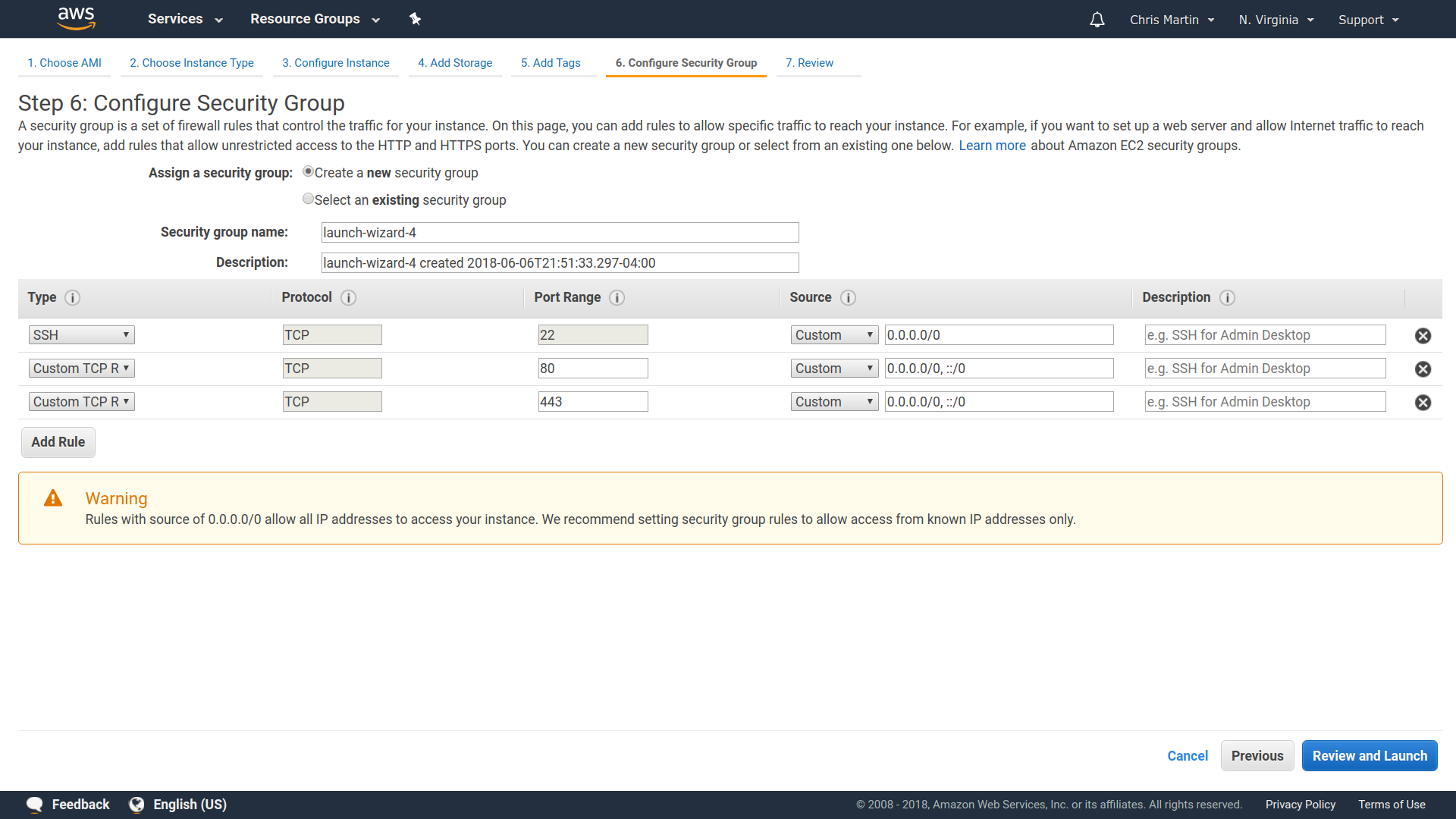
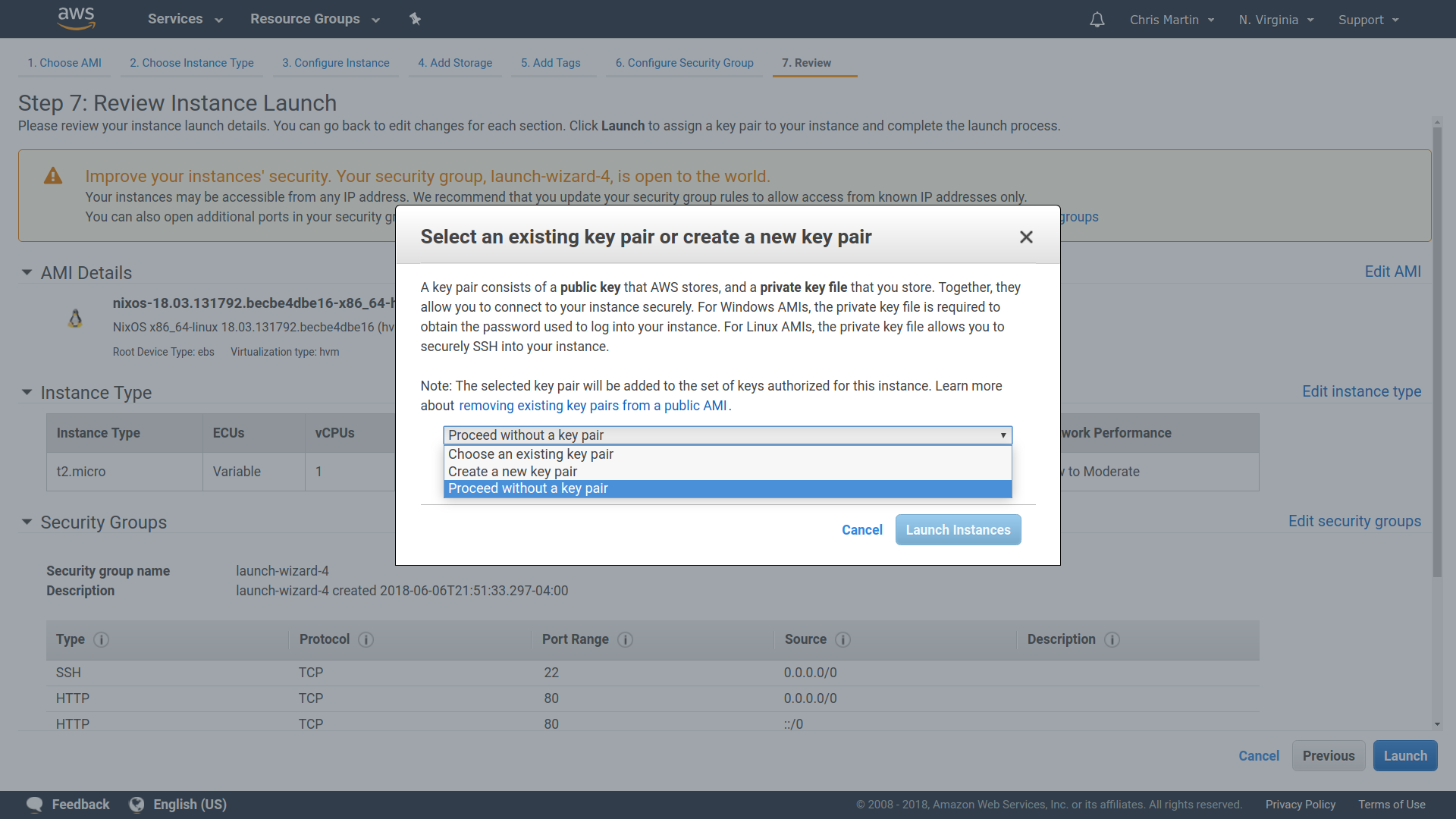
Building NixOS locally
❮bash❯ nix-build server.nix
[... a bunch of build output ...]
/nix/store/bbcbh0vv64v5bgdhdd4a8fw3p438iiam-nixos-system-unnamed-18.03.132618.0f73fef53a9
❮bash❯ ls -lh
ls -lh
total 12K
-rw-r--r-- 1 chris users 2.2K Jun 7 02:30 bootstrap.nix
lrwxrwxrwx 1 chris users 89 Jun 7 02:35 result -> /nix/store/pvf3l9x8m2fnw7l07g1yxw1iilj3m2rp-nixos-system-unnamed-18.03.132618.0f73fef53a9
-rw-r--r-- 1 chris users 176 Jun 7 02:30 server.nix
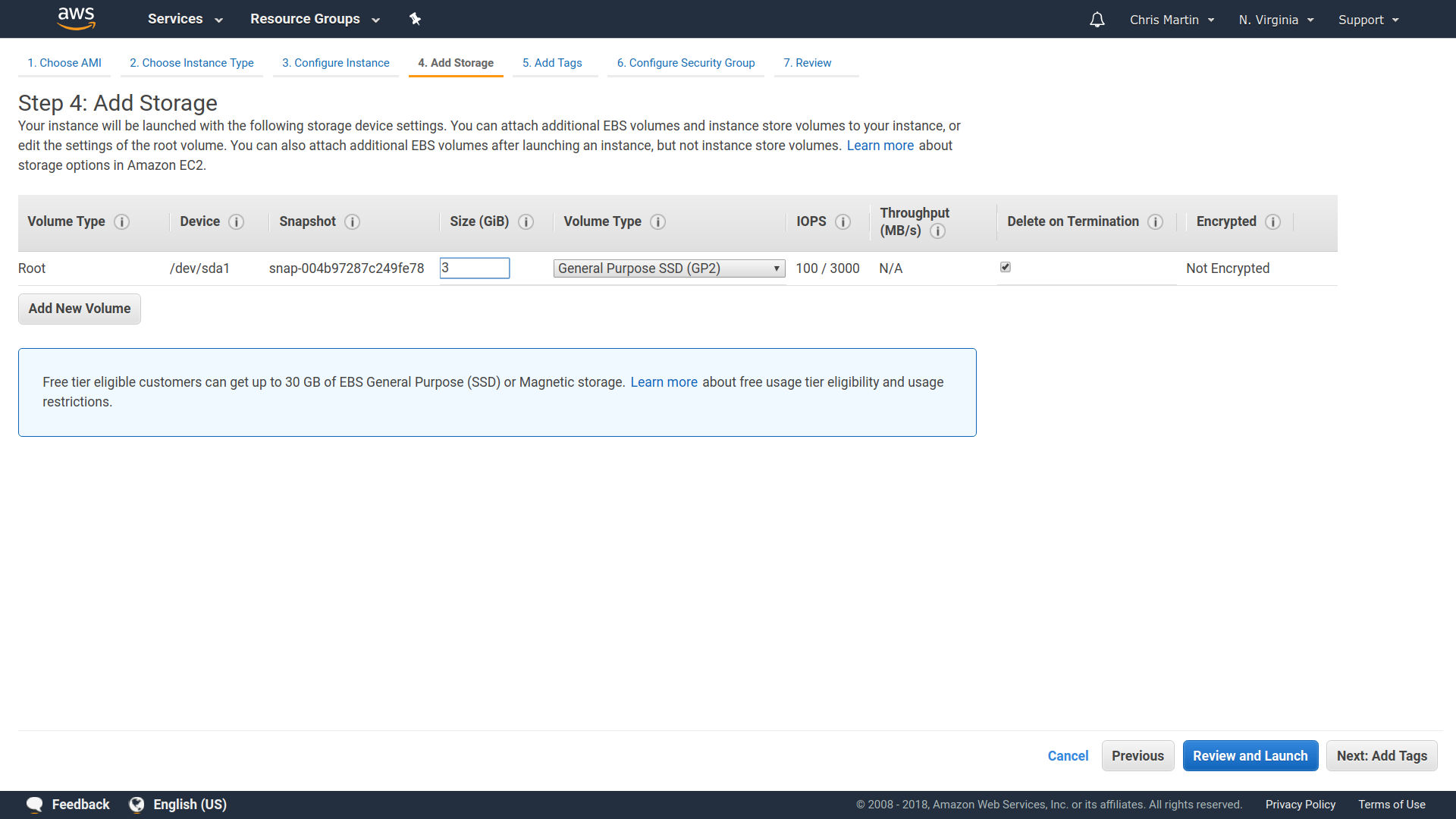
The build result
❮bash❯ ls -lh result/
total 60K
dr-xr-xr-x 2 root root 4.0K Dec 31 1969 bin
dr-xr-xr-x 2 root root 4.0K Dec 31 1969 fine-tune
-r-xr-xr-x 1 root root 13K Dec 31 1969 activate
lrwxrwxrwx 1 root root 91 Dec 31 1969 append-initrd-secrets -> /nix/store/m2jf41zpw52i10j01p4wij6j2h22721j-append-initrd-secrets/bin/append-initrd-secrets
-r--r--r-- 1 root root 0 Dec 31 1969 configuration-name
lrwxrwxrwx 1 root root 51 Dec 31 1969 etc -> /nix/store/iwpgvdg2i4vv6a0vd20d70425s0rifdh-etc/etc
-r--r--r-- 1 root root 0 Dec 31 1969 extra-dependencies
lrwxrwxrwx 1 root root 65 Dec 31 1969 firmware -> /nix/store/grzr4r1ajmnjjnq049r719jbj2p8zbcp-firmware/lib/firmware
-r-xr-xr-x 1 root root 4.9K Dec 31 1969 init
-r--r--r-- 1 root root 9 Dec 31 1969 init-interface-version
lrwxrwxrwx 1 root root 57 Dec 31 1969 initrd -> /nix/store/bnqw7sxz3pnakni5hmj22dqrqvjbbq1m-initrd/initrd
lrwxrwxrwx 1 root root 65 Dec 31 1969 kernel -> /nix/store/y0jcw44kw1962bdfnsayz1r6jsgz2sqj-linux-4.14.44/bzImage
lrwxrwxrwx 1 root root 58 Dec 31 1969 kernel-modules -> /nix/store/yw9zkbwkb76ypb0gvvakg0lkv1zirqg7-kernel-modules
-r--r--r-- 1 root root 51 Dec 31 1969 kernel-params
-r--r--r-- 1 root root 24 Dec 31 1969 nixos-version
lrwxrwxrwx 1 root root 55 Dec 31 1969 sw -> /nix/store/j85qcbjfwmis0c75qwbvxhirlj02kjmw-system-path
-r--r--r-- 1 root root 12 Dec 31 1969 system
lrwxrwxrwx 1 root root 55 Dec 31 1969 systemd -> /nix/store/cya0k4g78bd518wzgqghkk6srlvl2jgv-systemd-237
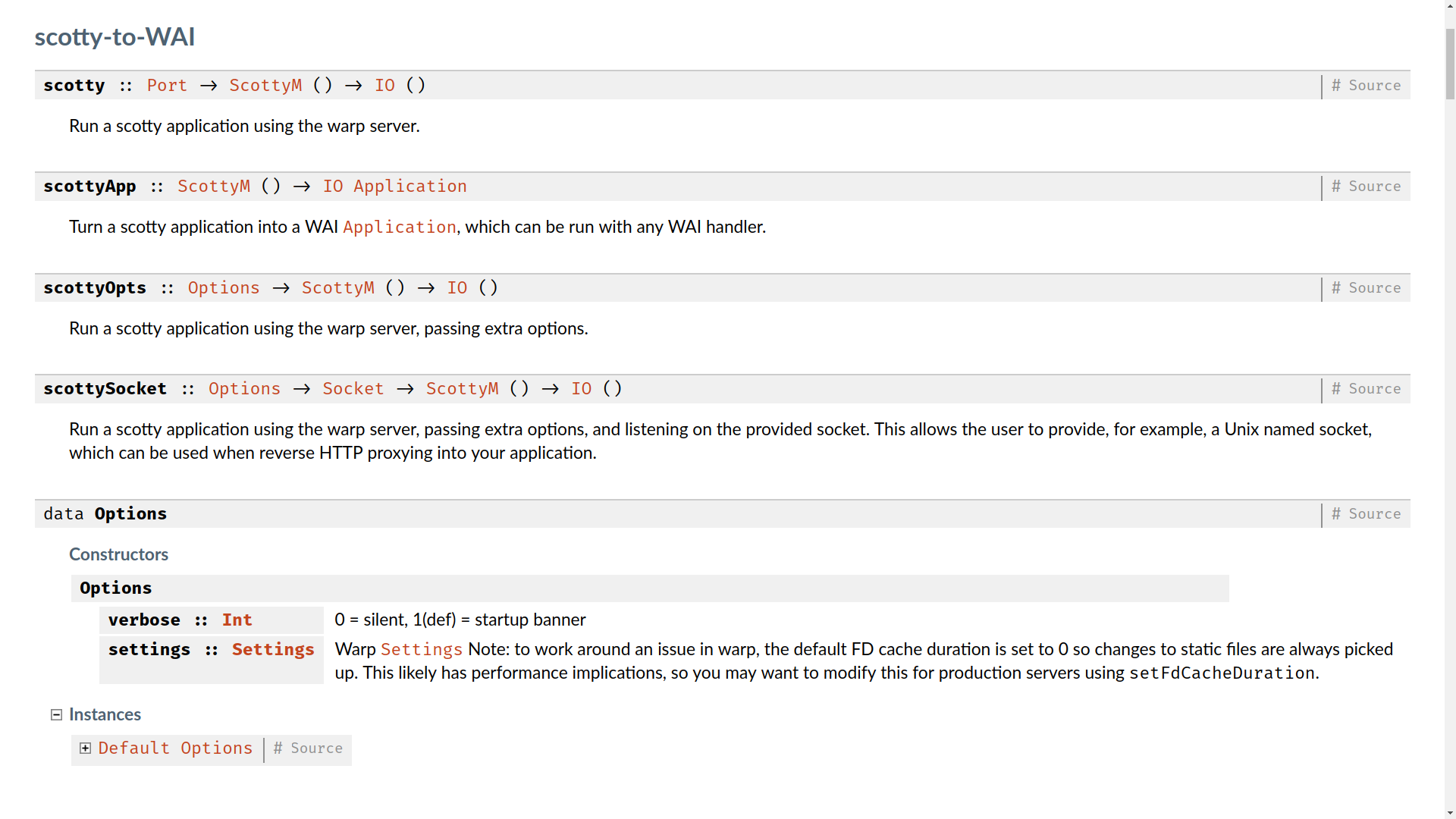
monadic-party/monadic-party.cabal
name: monadic-party
version: 0
cabal-version: >= 1.10
build-type: Simple
library
hs-source-dirs: lib
exposed-modules:
MonadicParty.Scotty
build-depends:
base
, neat-interpolation
, scotty
, text
ghc-options: -Wall
default-language: Haskell2010
executable party-scotty
hs-source-dirs: app
main-is: party-scotty.hs
build-depends:
base
, monadic-party
ghc-options: -Wall
default-language: Haskell2010